Unlocking the bootloader on unisoc T7510 is a prerequisite for many advanced actions, such as flashing Custom ROMs, rooting, or downgrading the operating system. Unlocking the bootloader will void your warranty, therefore you must be careful and take this into consideration.
The unlock method we share below is based on Vulnerabilities on BootROM Where an attacker with physical access to the device can replace a function pointer in the BootROM data section or a return address stored on the stack, allowing them to run their own code with the authority of the BootROM.
detailed Information about Vulnerabilities available here
unisoc BootROM can be taken from here or stack-info.csv.
Instructions
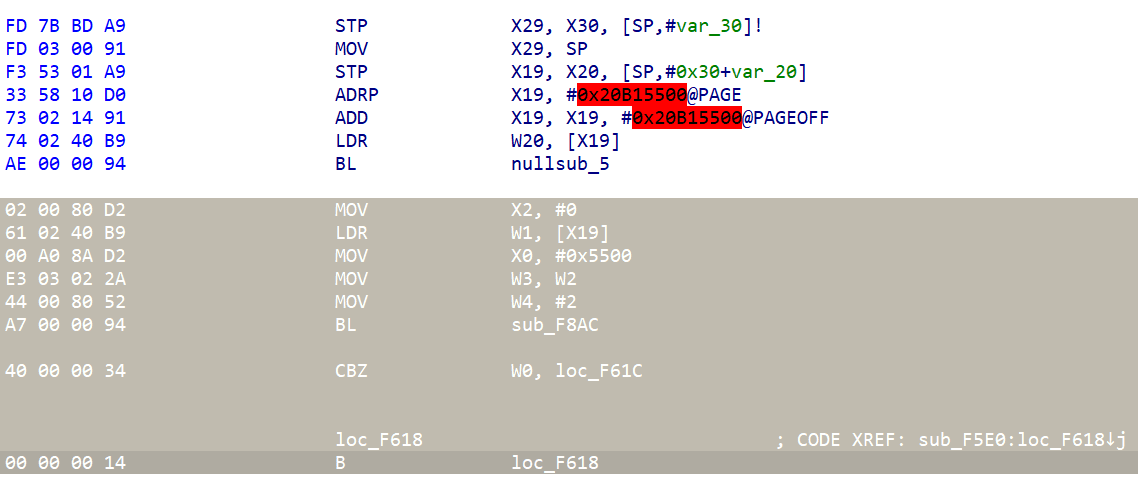
Step 1: overwrite stack to execute FDL1 without verfication
Use custom_exec_no_verify_3f88.bin to replace the stack if the device entered download mode by holding a specified button during startup (usually volume down).
Use custom_exec_no_verify_3f28.bin to replace the stack if the device entered download mode after all efforts to boot failed (for example, if the splloader was deleted and no key was hit).
Make custom_exec.bin in accordance with BootROM for more Socs affected by CVE-2022-38694.
Step 2: Modify FDL1
Patch 1: NOP(1F 20 03 D5) verfication in data_exec.
Patch 2: change download mode (0x102)(40 20 80 52) to boot mode(0x104)(80 20 80 52).
- Apply patch 1 to original FDL1, save as fdl1-dl.bin.
- Apply patch 1 and patch 2 to original FDL1, save as fdl1-boot.bin.
Using FDL1 from a different model (same Soc) appears secure. Unfortunately, only in download mode. Device-specific fdl1 is required to unlock the bootloader. If your manufacturer won’t provide fdl1, you can compile it yourself (you’ll need to modify some ddr init code to work with splloader).
Here is pre patched unlock tool for some devices
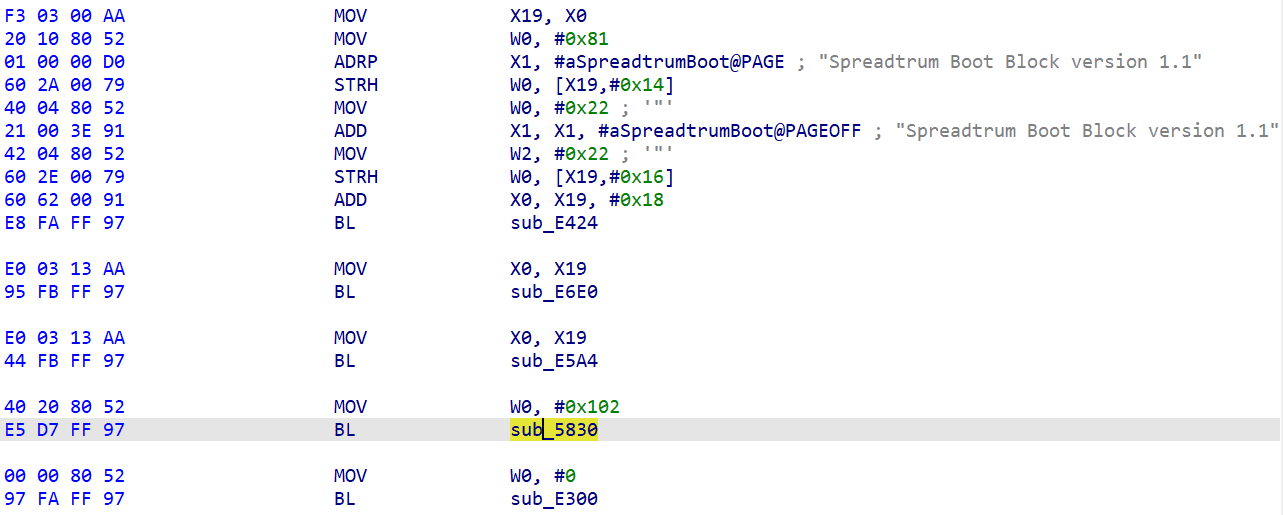
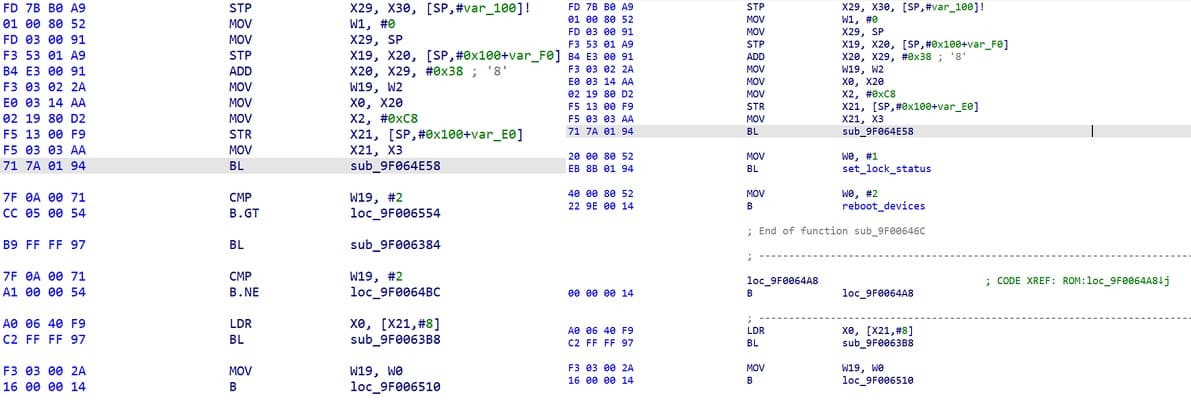
Step 3: Modify FDL2(uboot)
Patch 1: patch do_cboot.
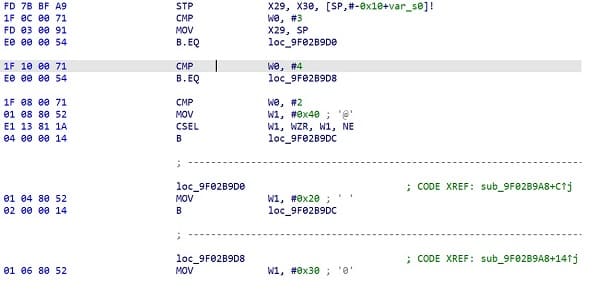
search for VerifiedBoot-UNLOCK to find set_lock_status.
search for 0x32121BAC or 0x1BAC (T7510 specific address ?), and reboot_devices starts with CMP W0,#3 CMP W0,#4 CMP W0,#2.
search for enter boot mode to find do_cboot, patch it to call set_lock_status and reboot_devices.
Patch 2 : NOP write check of secure partitions.
Like fdl1, uboot for unlocking bootloader (boot mode) must be device-specific as well. However, you can use another model (same Soc) uboot in download mode to read_part your device uboot
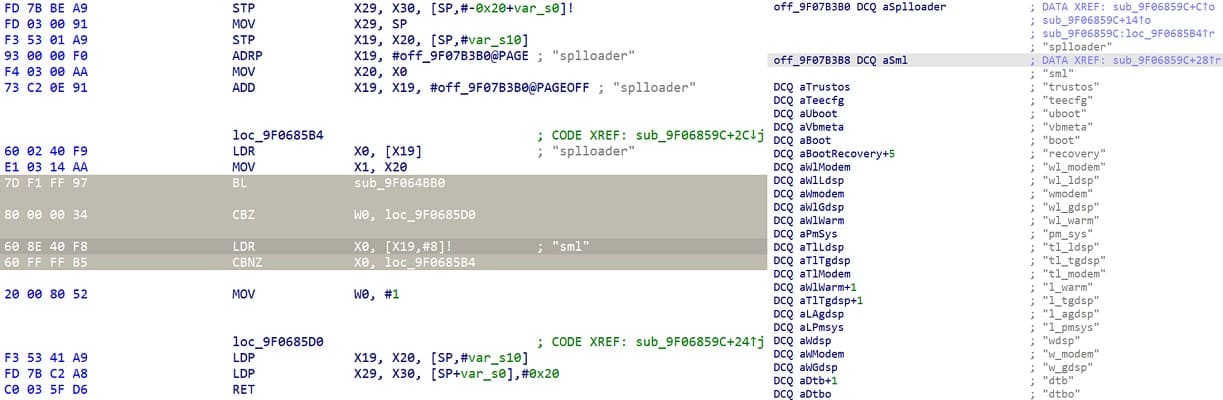
Part 4: get trustos images list and load address from splloader
get splloader by read_part
The list and address are easy to get, since _start calls reset, reset calls nand_boot, nand_boot will load images from emmc/ufs to memory and boot.
| device | model | android | sml | teecfg | tos |
|---|---|---|---|---|---|
| tyyh2020 | ud710_20c10 | 9 | 0x94000000 | no need | 0x94040000 |
| tyyh2021 | ud710_7h10 | 10 | 0x94000000 | 0x94020000 | 0x94040000 |
| Hisense A7 | ud710_2h10 | 10 | 0x94000000 | 0x94020000 | 0x94040000 |
Misc: you need to know correct partition size to read_part, this can be done by read_part user_partition 0 17K efi_part.img(It works for emmc, I don’t know about ufs). Open efi_part.img in WinHex.
Prepare unlock command
1: send fdl1-dl.bin, send uboot, read_part trustos images and chsize these images
2: send fdl1-boot.bin, send modified uboot with trustos images, sml must be the last one sent to device.
3: erase userdata, use one of download/fastboot/recovery (If your userdata use f2fs format, you can take the userdata.bin from tyyh branch).
Here is command that can be used with SPD_dump (must replaced with your own data)
Read Part:
spd_dump fdl fdl1-dl.bin 0x5500 fdl fdl2-dl.bin 0x9efffe00 exec read_part splloader 0 1m spl.bin read_part uboot_a 0 3m uboot.bin erase_part splloader reset
Write part
spd_dump fdl fdl1-dl.bin 0x5500 fdl fdl2-dl.bin 0x9efffe00 exec write_part uboot_a fdl2-cboot.bin write_part uboot_b fdl2-cboot.bin reset spd_dump fdl fdl1-dl.bin 0x5500 fdl fdl2-dl.bin 0x9efffe00 exec write_part splloader spl.bin write_part uboot_a uboot.bin write_part uboot_b uboot.bin reset
Method 2:
- use Online bootloader unlocker
Credit: Github users > TomKing062, Alephgsm, Iscle
Related:
- Mediatek BootROM
- Mediatek BootROM bypass Solution
- What is MediaTek Preloader? How to Install MediaTek Preloader Driver